-
Posts
4379 -
Joined
-
Last visited
-
Days Won
27
Content Type
Profiles
Forums
Downloads
Store
Gallery
Bug Reports
Documentation
Landing
Everything posted by ljm42
-

[6.12.10] Can't update docker container with port in URL
ljm42 commented on [email protected]'s report in Stable Releases
Many improvements have been made to Docker since the original report. If you are still having the issue in Unraid 6.12.10, please post diagnostics and updated screenshots / details. -
This thread is perfect for quick questions or comments, but if you suspect there will be back and forth for your specific issue, please start a new topic. Be sure to include your diagnostics.zip.
-
When the problem is occurring, please SSH in and run: /etc/rc.d/rc.nginx restart What is the response, and does it help? Also please run: cat /var/log/nginx/error.log and copy/paste the results back here. There is a lot of noise in this file but maybe something useful.
-
Please start a new thread in General Support, include as much detail as you can along with your diagnistics.zip (can get from SSH by typing "diagnostics", any questions go ahead and ask in your new thread to avoid a lot of back and forth in this announce post)
-
This thread is perfect for quick questions or comments, but if you suspect there will be back and forth for your specific issue, please start a new topic. Be sure to include your diagnostics.zip.
-
When you are ready to try again, be sure to grab your diagnostics.zip (from Tools -> Diagnostics) while in the new version. Then start a new thread under General Support, describe the issue and upload the diagnostics.
-
I'm confused about that first screenshot, did you actually see that or did you grab it from another post somewhere?
-

Switch from Self-Signed Certificate to Unraid LE (Solved)
ljm42 replied to karash's topic in General Support
This is correct. The certificate_bundle.pem cert is ONLY valid for *.myunraid.net urls. There is zero benefit to using it with other urls. If you access the server by IP address or by name then it will use a self-signed cert. It is fully setup. To use it, click the url starting with https://192-168... that you blanked out of the screenshot. For more information, see https://docs.unraid.net/unraid-os/manual/security/secure-webgui-ssl/ -
Keep playing with this, it should do what you want. The only other option is to change the IP in the client config but as you said it is not exactly secure. If you can't get it to work, try hosting VPN on your Unifi device instead.
-
Give IETF a try
-

Having Wireguard tunnel active stops server accessing the internet
ljm42 replied to Rkpaxam's topic in General Support
This is not normal. Do you have the WG Docker container enabled at the same time? Maybe there is some sort of conflict. I'd suggest stopping the Docker container and following the guide here to set up the built in one: https://forums.unraid.net/topic/84226-wireguard-quickstart/ Get "Remote access to LAN" working before trying something else. Read the entirety of the first two posts in that thread, there are many helpful tips that may point out an issue in your network. -
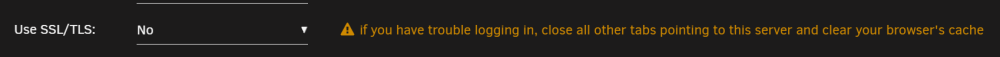
Are you changing SSL settings? The only cause I know of for what you are describing happens when you disable SSL, it can confuse your browser. To help prevent confusion, the webgui shows this message: If you are sure that is not the cause, go to Settings > Syslog Server and temporarily enable "Mirror syslog to flash". The next time it happens: 1) clear your browser's cache to see if that helps 2) if not, reboot the server and upload your diagnostics (from Tools -> Diagnostics) here Note: once you past this issue be sure to disable "Mirror syslog to flash" as it adds wear and tear to the flash drive
-
Think of Unraid as an appliance, not a general purpose operating system. If you need a place to perform "daily business" the recommendation would be to run a different OS in a VM.
-
Manual upgrade instructions are in the docs: https://docs.unraid.net/unraid-os/manual/upgrade-instructions/#manual-upgrade-or-downgrade It sounds like you might have skipped this step: Move (not copy) bz* and changes.txt from the root of the flash drive to the "previous" directory, overwriting files as needed If so, when you replaced the files in the root of the flash you overwrote the running OS. There is no graceful recovery for this. Your best bet would be to turn the system off, put the flash drive in a different computer, and follow those manual instructions from the top
-
Unraid 6.12.8 does not have proper support for Lifetime keys. Please upgrade to Unraid 6.12.10
-
Yes, this release is intended to resolve the issue with your drive controller: https://forums.unraid.net/topic/160471-unraid-os-version-61210-available/
-
Yes the update process isn't really setup for people to run in "pending restart" mode for an extended period. TBH this could confuse plugins and other things that aren't prepared for this as well, I would not recommend updating the OS until you are ready to restart. 6.12.9 does have an issue with certain Asmedia controllers, if you are at all concerned about that you can go to Settings -> Disk Settings and disable array autostart. Then when it boots into 6.12.9 there will be no problems and you can just run the update to 6.12.10 and reboot into that.
-
Glad to hear it! Kudos to @Kilrah
-
This is suspect. Try manually stopping the container (reload the page and be sure it is really stopped) before doing the update and see if it makes a difference. Otherwise, I agree with the suggestion to recreate the docker image
-
Unraid 6.12.10 is now available:
-
Thanks, we got the feedback we needed and have published 6.12.10:
-
This release reverts to an earlier version of the Linux kernel to resolve two issues being reported in 6.12.9. It also includes a 'curl' security update and corner case bug fix. All users are encouraged to read the release notes and upgrade. Upgrade steps for this release As always, prior to upgrading, create a backup of your USB flash device: "Main/Flash/Flash Device Settings" - click "Flash Backup". Update all of your plugins. This is critical for the Connect, NVIDIA and Realtek plugins in particular. If the system is currently running 6.12.0 - 6.12.6, we're going to suggest that you stop the array at this point. If it gets stuck on "Retry unmounting shares", open a web terminal and type: umount /var/lib/docker The array should now stop successfully If you have Unraid 6.12.8 or Unraid Connect installed: Open the dropdown in the top-right of the Unraid webgui and click Check for Update. More details in this blog post If you are on an earlier version: Go to Tools -> Update OS and switch to the "Stable" branch if needed. If the update doesn't show, click "Check for Updates" Wait for the update to download and install If you have any plugins that install 3rd party drivers (NVIDIA, Realtek, etc), wait for the notification that the new version of the driver has been downloaded. Reboot This thread is perfect for quick questions or comments, but if you suspect there will be back and forth for your specific issue, please start a new topic. Be sure to include your diagnostics.zip.
-
Thanks, this link is part of the Unraid Connect plugin. It will be fixed in an upcoming plugin release. In the meantime, this link should do the trick: https://discord.unraid.net/
-

[6.12.9] Disks missing after upgrading to 6.12.9
ljm42 commented on mgrinspan's report in Stable Releases
Hi, please install 6.12.10-rc.1 and confirm it resolves the issue: https://forums.unraid.net/bug-reports/prereleases/unraid-os-version-61210-rc1-available-r2941/